Cyber compliance denotes the adherence to a framework of regulations, statutes, and industry standards designed to fortify digital infrastructure against cyber threats. This imperative arises from the legal and regulatory landscape, wherein non-compliance invites substantial penalties and legal liabilities.
The essence of cyber compliance lies in protecting sensitive information from unauthorized access and ensuring the integrity of digital systems. This entails not only meeting legal obligations but also safeguarding the trust and reputation of clients and stakeholders.


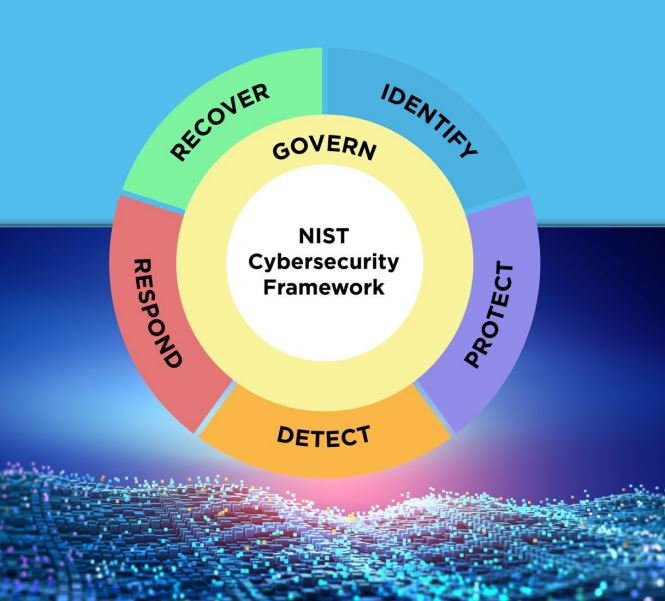
Under the NIST Cybersecurity Framework 2.0, Govern represents a new addition designed to emphasize the importance of oversight and accountability in cybersecurity. This update sends a clear message: cybersecurity is no longer just an IT issue—it’s a governance issue. The Govern function requires organizations to integrate cybersecurity into their leadership structure, ensuring executives are actively engaged in setting policies, managing risks, and overseeing incident responses. This proactive approach empowers decision-makers to not only mitigate risks but to also align cybersecurity practices with broader business objectives. For any company striving for resilience, Govern ensures that cybersecurity is embedded in every level of the organization, from the boardroom to the server room.
The Identify Function helps you determine the current cybersecurity risk to the business. Before you can protect your assets, you need to identify them. Then you can determine the appropriate level of protection for each asset based upon its sensitivity and criticality to your business mission.
The Protect Function supports your ability to use safeguards to prevent or reduce cybersecurity risks. Enabling multi-factor authentication (MFA) is one of the fastest, cheapest ways you can protect your data. Start with accounts that can access the most sensitive
The Detect Function provides outcomes that help you find and analyze possible cybersecurity attacks and compromises.
The Respond Function supports your ability to take action regarding a detected cybersecurity incident. Before an incident occurs, you want to be ready with a basic response plan.
The Recover Function involves activities to restore assets and operations that were impacted by a cybersecurity incident.
HIPAA Risk Assessment is a systematic evaluation process mandated by the Health Insurance Portability and Accountability Act (HIPAA) to identify and mitigate potential risks to the confidentiality, integrity, and availability of protected health information (PHI). It involves assessing security measures, identifying vulnerabilities, and implementing safeguards to ensure compliance with HIPAA regulations and protect patient data from unauthorized access or disclosure.
The Payment Card Industry Data Security Standard (PCI DSS) applies to organizations that handle credit card transactions, such as retailers, e-commerce platforms, and payment processors. PCI DSS outlines strict security measures, including encryption, monitoring, and vulnerability testing, that businesses must implement to protect cardholder data. Compliance is overseen by the PCI Security Standards Council, and non-compliance can lead to fines, increased transaction fees, or even the revocation of a company’s ability to process credit card payments.
PCI DSS compliance is not just a regulatory obligation—it’s essential for any business that wants to avoid the financial and reputational damage caused by a data breach. A single breach can expose thousands, if not millions, of credit card numbers, leading to significant financial loss for consumers and businesses alike. By adhering to PCI DSS, organizations demonstrate their commitment to protecting customer information and maintaining the trust necessary for successful commercial operations.
The NYSDFS CRR 500 Assessment and Compliance pertains to the cybersecurity regulations set forth by the New York State Department of Financial Services (NYSDFS). It requires financial institutions operating in New York to establish and maintain a robust cybersecurity program to protect sensitive data and systems from cyber threats. Compliance involves conducting risk assessments, implementing security measures, and reporting incidents to ensure the integrity and confidentiality of customer information. This framework aims to enhance cybersecurity resilience within the financial sector and safeguard against cyberattacks.
FINRA (Financial Industry Regulatory Authority) Assessment and Compliance involve adhering to regulations and standards set by FINRA, a self-regulatory organization overseeing broker-dealers and securities firms in the United States. Compliance requires implementation of measures to ensure the integrity, confidentiality, and availability of financial data and customer information. This includes conducting risk assessments, establishing cybersecurity policies and procedures, and providing training to employees. Compliance demonstrates a commitment to regulatory requirements and helps protect investors and maintain market integrity within the financial industry.
The Gramm-Leach-Bliley Act (GLBA) is primarily focused on financial institutions, ensuring that they protect consumer data through a combination of privacy rules and security measures. Under the GLBA, financial institutions must safeguard sensitive customer information, both when it is stored and when it is in transit. This includes providing customers with clear notices about their privacy practices and giving them the ability to opt out of sharing information with non-affiliated third parties. The Safeguards Rule within the GLBA is what really gets into the nuts and bolts of cybersecurity, requiring institutions to develop, implement, and maintain an information security program.
For financial entities, compliance with the GLBA isn’t optional; it’s essential for maintaining consumer trust. Banks, credit unions, and insurance companies are lucrative targets for cybercriminals because of the vast amounts of financial data they handle. The GLBA compels these institutions to adopt proactive cybersecurity measures to mitigate risks like data breaches, phishing attacks, and insider threats. But more than just legal compliance, the GLBA fosters a broader culture of transparency, making it clear to customers that their financial information is being handled with care.
The Children’s Online Privacy Protection Act (COPPA) places strict requirements on websites and online services that collect personal information from children under 13 years of age. The act requires these services to obtain verifiable parental consent before collecting, using, or disclosing a child’s personal information. COPPA also mandates that these platforms implement reasonable cybersecurity measures to protect the data they collect.
For businesses operating online, COPPA compliance is a serious responsibility. The rise of digital platforms that target younger audiences has made children a prime target for cyber threats, including identity theft and exploitation. By requiring companies to safeguard children’s data and obtain parental consent, COPPA not only protects children’s privacy but also holds businesses accountable for how they manage this particularly sensitive demographic’s information.
The Children’s Internet Protection Act (CIPA) is a federal law that requires schools and libraries to implement internet safety policies as a condition for receiving certain federal funding. The CIPA isn’t just about filtering inappropriate content—it’s about protecting the digital well-being of minors in a rapidly evolving online world. Schools and libraries must block harmful content like pornography and cyberbullying while also educating students on proper online behavior. Compliance with CIPA goes beyond technology; it demands an ongoing commitment to creating a safe and informed online environment for young users. For institutions that rely on federal funding, adhering to CIPA is not only legally necessary but also ethically crucial in safeguarding children in today’s digital age.
The Federal Trade Commission Act (FTC Act) empowers the FTC to take action against companies that engage in unfair or deceptive practices, including inadequate cybersecurity measures. While the FTC Act is not a cybersecurity law per se, it has been used to enforce penalties against companies that fail to protect consumer data or mislead customers about their security practices. In several high-profile cases, the FTC has brought enforcement actions against businesses that suffered data breaches as a result of insufficient security measures.
For businesses, the FTC Act serves as a warning that cybersecurity is not just an IT issue—it’s a consumer protection issue. Companies that fail to invest in adequate cybersecurity measures or that misrepresent their security practices can find themselves facing FTC investigations, costly fines, and significant reputational harm. The FTC Act essentially makes clear that cybersecurity is a core component of modern business ethics and consumer protection.
The New York SHIELD Act (Stop Hacks and Improve Electronic Data Security Act) expands upon existing data breach notification laws by requiring businesses that collect personal information from New York residents to implement reasonable security measures. The SHIELD Act applies to any business handling private data, not just those physically located in New York. It defines “private information” broadly, including biometric data, login credentials, and even medical information. The act also introduces stronger breach notification requirements, mandating that businesses inform affected individuals in a timely manner.
NIST (National Institute of Standards and Technology) Security Documentation Development involves creating comprehensive security documentation based on guidelines provided by NIST. This process includes developing policies, procedures, guidelines, and standards to address various aspects of information security, such as risk management, access control, incident response, and security awareness training. The documentation typically aligns with NIST Special Publication 800 series, which provides detailed guidance on cybersecurity best practices. By following NIST standards, organizations can enhance their security posture, mitigate risks, and ensure compliance with regulatory requirements.
Indeed, cyber security and compliance represent ongoing endeavors rather than one-time tasks. The ever-evolving nature of cyber threats and regulatory landscape necessitates continual assessment, adaptation, and improvement of security measures and compliance efforts. Organizations must remain vigilant, proactive, and responsive to emerging risks, technological advancements, and regulatory changes. By adopting a dynamic and iterative approach to cyber security and compliance, businesses can effectively mitigate risks, protect sensitive data, and uphold trust and integrity in the digital realm.
For over 30 years, liquidcoretechservice has worked alongside clients nationwide to develop solutions to meet all of their technology and telecommunications needs.
At Liquid Core Tech Services, we are committed to delivering resilient, secure, and straightforward solutions that empower you to thrive in today’s digital landscape.
Copyright © 2024 Liquid Core Tech Services LLC